Membuka wawasan ilmu dan teknologi dari kehidupan sehari-hari....expand your mind.
Rabu, 31 Agustus 2011
Sony shows wearable 3-D personal theater
Selasa, 30 Agustus 2011
Komputasi Awan Cocok untuk Lembaga Pendidikan
Komputasi Awan Cocok untuk Lembaga Pendidikan
Meski infrastruktur masih jadi kendala, perkembangan Internet ke depan akan membaik.

VIVAnews - Sistem komputasi awan untuk penyimpanan data sebuah institusi perlu didukung oleh kemudahan infrastruktur internet, termasuk tarif internet yang terjangkau. Namun, selain dukungan infrastruktur, perlu juga diperhatikan aspek security atau keamanannya.
“Sistem cloud akan semakin berkembang, tetapi perlu memperhatikan juga seputar security-nya,” kata Guru Besar Sistem Manajemen Informatika Binus University, Harjanto Prabowo, di Jakarta, Selasa, 25 Agustus 2011.
Meski masalah infrastruktur masih menjadi kendala di Indonesia, Harjanto meyakini, perkembangan Internet ke depan akan semakin membaik.
“Komputasi awan memang akan memudahkan korporasi atau perusahaan dalam menyimpan data. Tetapi, akan lebih baik lagi bila komputasi awan dioptimalkan fungsinya. Tidak hanya untuk penyimpanan data,” kata Harjanto.
Cloud, kata Harjanto, bisa dibuat menjadi aplikasi yang lebih sempurna. “Hardware-nya sudah mahal, jadi sebaiknya jangan dipakai untuk storage saja,” ucapnya. “Selain security, cloud computing juga perlu dibarengi dengan etika, agar tidak disalahgunakan untuk kejahatan,” ucapnya.
Saat ini, Harjanto menyebutkan, pihaknya telah menerapkan sistem cloud computing atau komputasi awan, khususnya untuk mengelola data mahasiswa.
“Dengan jumlah mahasiswa mencapai 24 ribu, pengelolaan akan lebih mudah jika menggunakan sistem komputasi awan,” kata Harjanto. “Kami pakai itu untuk mengelola dan menyimpan karya dari 24 ribu mahasiswa,” ucapnya. (art)
Bosscha: Lebaran Jatuh pada 31 Agustus 2011
BERITA NASIONAL LAINNYA
Pelabuhan Merak Padat, Pemudik Kesal
Liputan 6 - Sen, 29 Agu 2011Panti Asuhan Terbakar, Penghuni Pingsan
Liputan 6 - Sen, 29 Agu 2011Jemaah Naqsabandiyah Padang Lebaran Senin Ini
Liputan 6 - Sen, 29 Agu 2011
Ngamprah (ANTARA) - Peneliti Observatorium Bosscha Bandung, Jawa Barat, Deva Octavian menegaskan bahwa hari lebaran 2011 atau 1 syawal 1432 Hijriah akan jatuh pada 31 Agustus 2011.
Penentuan itu merupakan hasil dari pengamatan dengan menggunakan pisau analisis ilmu astronomi yang dimilikinya. Oleh karena itu, ijtimak akhir Ramadhan 1432 Hijriah akan dilakukan pada Senin 29 Agustus pukul 10.04 WIB.
"Tinggi bulan saat matahari terbenam 29 Agustus di seluruh wilayah Indonesia kurang dari dua derajat. Dari data tersebut, hilal tidak mungkin dilihat di wilayah Indonesia. Dengan begitu, 1 Syawal 1432 Hijriah tanggal 30 Agustus setelah Maghrib. Jadi, masih ada Salat Tarawih pada 29 Agustus dan tidak ada tarawih tanggal 30 Agustus," ujarnya.
Dengan demikian sambungnya, puasa pada tahun 1432 Hijriah berjumlah 30 hari. Meski begitu, rencananya sidang itsbat penentuan 1 Syawal 1432 Hijriah akan dilakukan pada 29 Agustus.
"Makanya, tidak salah kalau yang menggunakan metode hisab dan rukyatul hilal dalam penentuan awal syawal akan berbeda. Sebab, 29 Agustus, hilal belum terlihat oleh mata karena dekat dengan matahari," katanya.
Pimpinan Pusat Muhammadiyah, Abdul Fattah Wibisono mengatakan, Muhammadiyah sudah menentukan bahwa hari raya tahun ini jatuh pada Selasa (30/8).
Keputusan itu merupakan hasil perhitungan hisab tim Muhammadiyah. Saat matahari terbenam pada hari ke-29 Ramadhan, posisi hilal ada di atas ufuk dengan ketinggian 1 derajat 55 menit.
35 petugas
Sebelumnya, Peneliti observatorium Bosscha Bandung, Deva Octavian mengatakan 35 orang akan diterjunkan dalam penentuan hari lebaran atau 1 syawal 1432 Hijirah. Personil sebanyak itu akan mengamati hilal pada 16 titik yang telah ditentukan.Jumlah sebanyak itu merupakan gabungan dari Kementerian Komunikasi dan Informatika (Kemenkominfo), Observatorium Bosscha, Rukyatul Hilal Indonesia, Lapan, serta sejumlah perguruan tinggi. Sedangkan untuk pengamatan hilal akan dilakukan pada 29 dan 30 Agustus mulai pukul 16.00 WIB.
"Secara prinsip kerja dalam penentuan hari awal puasa dengan lebaran atau 1 syawal tidak ada bedanya karena sama-sama mengamati hilal," ujarnya.
Jumlah pengamat dan titik pengamatan hilal untuk penentuan 1 syawal 1432 Hijriah lebih banyak dari pada pengamatan hilal untuk menentukan awal Ramadhan yang hanya melibatkan 30 orang untuk 14 titik saja. Disampaikannya, Kemenkominfo memang sengaja memperbanyak jumlah titik pengamatan hilal, hal itu karena lebih mempermudah pengamatan dan menjamin ketepatannya. Karena bisa jadi, pengamatan yang dilakukan di suatu daerah terhalangi, tapi di daerah lainnya bisa dilakukan.
http://id.berita.yahoo.com/bosscha-lebaran-jatuh-pada-31-agustus-2011-092609123.html
Fish-catching trick may be spreading among dolphins
PERTH, Australia (Reuters) - Dolphins in one western Australian population have been observed holding a large conch shell in their beaks and using it to shake a fish into their mouths -- and the behavior may be spreading.
Researchers from Murdoch University in Perth were not quite sure what they were seeing when they first photographed the activity, in 2007, in which dolphins would shake conch shells at the surface of the ocean.
"It's a fleeting glimpse -- you look at it and think, that's kind of weird," said Simon Allen, a researcher at the university's Cetacean Research Unit.
"Maybe they're playing, maybe they're socializing, maybe males are presenting a gift to a female or something like that, maybe the animals are actually eating the animal inside."
But researchers were more intrigued when they studied the photos and found the back of a fish hanging out of the shell, realizing that the shaking drained the water out of the shells and caused the fish that was sheltering inside to fall into the dolphins' mouths.
A search through records for dolphins in the eastern part of Shark Bay, a population that has been studied for nearly 30 years, found roughly half a dozen sightings of similar behavior over some two decades.
Then researchers saw it at least seven times during the four-month research period starting this May, Allen said.
"There's a possibility here -- and it's speculation at this stage -- that this sort of change from seeing it six or seven times in 21 years to seeing it six or seven times in three months gives us that tantalizing possibility that it might be spreading before our very eyes," he added.
"It's too early to say definitively yet, but we'll be watching very closely over the next couple of field seasons."
The Shark Bay dolphin population is already unusual for having developed two foraging techniques, one of which involves the dolphin briefly beaching itself to grab fish after driving them up onto the shore.
The other is "sponging" -- in which the dolphins break off a conical bit of sponge and fit it over their heads like a cap, shielding them as they forage for food on the sea floor.
But both of these spread "vertically," mainly through the female dolphin population, from mother to daughter. The intriguing thing about this new behavior with the conch shells is that it might be spreading "horizontally," Allen said.
"If it spreads horizontally, then we would expect to see it more often and we'd expect to see it between 'friends'," he added, noting that dolphins are known for having preferences in terms of companions and whom they spend time with.
"Most of the sightings from this year are in the same habitat where we first saw it in 2007, and a couple of the individuals this year are known to associate with the ones that we saw doing it a year or two ago."
The next step would be not only to observe the behavior again in another season but also to try and gather evidence Of deliberate actions on the part of the dolphins.
"If we could put some shells in a row or put them facing down or something like that and then come back the next day, if we don't actually see them do it but find evidence that they've turned the shell over or make it into an appealing refuge for a fish, then that implies significant forward planning on the dolphins' parts," Allen said.
"The nice idea is that there is this intriguing possibility that they might manipulate the object beforehand. Then that might change using the shell as just a convenient object into actual tool use," he added.
(Reporting by Elaine Lies; Editing by Alex Richardson)
http://news.yahoo.com/fish-catching-trick-may-spreading-among-dolphins-080748681.html
Upgrade Your Life: 5 ways to make an easy-to-remember, ultra-secure password
Upgrade Your Life: 5 ways to make an easy-to-remember, ultra-secure password
By Taylor Hatmaker, Tecca | Upgrade Your Life – Wed, Aug 24, 2011Nobody wants to get hacked. But when it comes to choosing a password, there are key steps you can take to reduce your risk of data intrusions from unwanted virtual visitors. This week's edition of Upgrade Your Life will teach you how to make a strong, safe password that's easy to remember — and how to reduce your odds of being an easy target for hackers.
1. Worst Passwords
In 2009, a major hack on social gaming site RockYou revealed some troubling patterns in how we choose our passwords. The Imperva Application Defense Center (ADC), a security research group, examined the passwords of RockYou's clients to see just what went wrong. The study found that more than 29,000 of the compromised accounts were using the password "123456" — the most popular password. The second and third most common passwords were also strings of consecutive numbers. And the fourth most common password? "Password." Other popular passwords from the RockYou case include "iloveyou," "abc123," and a handful of common first names like "Ashley" and "Michael."
How to avoid bad passwords:
* Don't use any part of your name or email address: These two pieces of information are easily obtained about you.
* Avoid any other personal information: Don't use your birthday, family member or pet names, street addresses, or anything else that could be public knowledge for prying eyes.
* Don't use consecutive numbers: These are extremely easy for a cracking program to decode, and as you can see from the ADC study, they're also wildly popular.
* Avoid words in the dictionary: This includes random sequences of words and slang terms too.

2. Best Passwords: Uppercase and lowercase letters, numbers, and symbols
Nowadays, many websites encourage good password practices by forcing you to input a mix of numbers, letters, symbols, and mixed capitalization. This approach is definitely the right idea: mixing it up can pay off, statistically speaking. Why? Most password hacks you'll be warding off use a technique called a "brute force attack." This flavor of hack uses automated computer software to guess every possible combination to crack your personal code.
According to the ADC study, automated hacking software combined with poorly chosen passwords means a hacker can break into 1000 accounts in just 17 minutes. If you introduce more variables into your password — namely numbers, symbols, and a mix of lower and upper case letters — intrusive software will take longer to crack your code.
Make passwords more secure:
* Add letters: Since there are 26 letters in the alphabet, one additional letter can make your password 26 times harder to crack.
* Use a mix of lower and uppercase letters: Mixing up your cases adds complexity and safety to your chosen password.
* Add numbers: Using letters, words, and phrases for your passwords seems both natural and easy to remember, but it's much safer to diversify.
* Add symbols: Symbols are the real secret ingredient to security. Since there are over 1500 symbols a hacking program needs to run through to correctly lock down one character of your password, adding one extra asterisk or exclamation point can make it 1500 times more difficult for intruders to pry open your personal accounts.
3. Password length = Password strength
Most websites prompt you to create a code with a minimum and maximum amount of characters, often between 8 and 14. Since each additional character increases your odds of staying safe, be sure to max out the length of your password. If you can enter 14 characters, don't stop at 10 — those extra 4 characters will work to your statistical advantage.
Here's an example: compare the passwords m00se44 verses m00se44!.!.!.!
Sure m00se44 might be faster to type, but m00se44!.!.!.! is a far safer bet. How much safer? According to a handy online brute force simulator, hackers could crack m00se44 in less than a second. What about m00se44!.!.!.!? Assuming that the hacking software is guessing one hundred billion combinations a second, believe it or not, it could take the same software almost 200,000 centuries to crack it.
4. Password padding: Symbols are your secret weapon
Much of the basis for this article comes from the research of a noted security expert named Steve Gibson. His most recent practical advice involves a simple technique called "password padding." It used to be that a random password like Pr5^w4''t3F was perceived to be the best password. But the reality is that people can't actually remember those totally random passwords, so they don't end up using or sticking with them.
To solve this dilemma, Gibson wanted to create a memorable password strategy that would be equally secure. He stumbled onto the idea that long passwords loaded with symbols can be both ultra-secure and yet also easily memorized. He came up with the following example to prove his point.
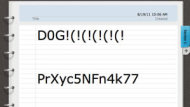
Which of these is easier to remember? Which is more secure?
D0g!(!(!(!(!(!
PrXyc5NFn4k77
The more memorable password is D0g!(!(!(!(!(! since it looks like the familiar word "dog" and ends with a repeating pattern of symbols. And according to Gibson, D0g!(!(!(!(!(! is also the more secure password because, while it too has numbers, letters (upper and lowercase), and symbols, the first example is one character longer than the random second password — and it has more symbols.
Want to see this effect in action? Play around with Gibson's password security calculator yourself.
5. Store passwords in one place with a password manager
If you're a little concerned about juggling all of the lengthy, ultra-secure passwords you've dreamed up, you can have a program do the heavy lifting. These programs and apps, known as password wallets or password managers, lock down your cache of codes by encrypting them, which translates them into a secure language that hackers can't parse. If RockYou's data had been encrypted, that security scandal could have been avoided altogether.
While no method is infallible, well-regarded password managers like LastPass and 1Password are great options. With a password manager, you'll use a master password to access the program or app, and it will auto-fill password entry fields for you as you log in around the web. Both LastPass and 1Password feature mobile and desktop versions, so you can keep both computer and your phonelocked down safely.
Senin, 29 Agustus 2011
Yuk, Pantau Hilal 1 Syawal Via Web
Yuk, Pantau Hilal 1 Syawal Via Web
Rachmatunisa - detikinet

situs pemantauan hilal
Hilal adalah penanda masuknya bulan baru pada kalender Hijriah. Banyak kegiatan penting ke-Islam-an mengambil dasar posisi Bulan di langit, seperti Tahun Baru Hijriah, awal puasa Ramadhan, dan tentu saja Hari Raya Idul Fitri dan Idul Adha.
Agar informasi hilal astronomi dapat tersampaikan lebih luas dan terbuka kepada masyarakat, Kementerian Komunikasi dan Informatika (Kominfo)bekerjasama dengan PT Telkom, Observatorium Bosscha serta Fakultas MIPA ITB menyediakan relay video streaming pengamatan hilal astronomi di halaman web.
Saat ini ada empat situs yang menyediakan tayangan pengamatan hilal. Keempat situs itu adalah Kominfo dihttp://hilal.kominfo.go.id, situs peneropongan bintang Bosscha dan Institut Teknologi Bandung yang beralamat di http://bosscha.itb.ac.id/hilal, situs milik Badan Meterologi dan Geofisika (BMKG) http://bmkg.go.id dan situs yang beralamat di http://rukyatulhilal.org
Pelaksanaan pengamatan hilal didukung oleh Kemenag, LAPAN, BMKG, Universitas Islam Negeri Sultan Syarif Karim, Rukyatul Hilal Indonesia, Universitas Mataram, Universitas Hasanuddin, Universitas Pendidikan Indonesia dan Universitas Lampung.
Pemantauan hilal dilakukan di 14 titik lokasi pengamatan di Indonesia, yakni:
1. Lhoknga, Aceh
2. UIN Suska, Pekanbaru, Riau
3. Dermaga TPI Perkemas Kalianda, Lampung
4. UPI Bandung, Jabar
5. Observatorium Bosscha Lembang, Bandung, Jabar (Information Center)
6. SPD Lapan Pameungpeuk, Jabar
7. Pelabuhan Ratu, Sukabumi, Jabar (1 Syawal 1432H)
8. Bukit Bela Belu, D.I. Yogyakarta
9. Denpasar, Bali
10. Mataram, NTB
11. Kupang, NTT
12. SPD Lapan Pontianak, Kalbar
13. Makassar, Sulser
14. SPD Lapan Biak, Papua
Sidang itsbat untuk menentukan jatuhnya Hari Raya Idul Fitri digelar Kemenag sore ini. Sidang yang dipimpin oleh Menteri Agama Suryadharma Ali tersebut dimulai pukul 16.30 WIB dengan acara presentasi mengenai hasil pengamatan hilal. Setelah dipotong oleh buka puasa bersama, sidang akan kembali dibuka pada pukul 19.00 WIB.
( rns / vit )
Sabtu, 27 Agustus 2011
5 Tips Berkirim Surel (Surat Elektronik)
5 Tips Berkirim Surel (Surat Elektronik)
Pilihan lain adalah menggunakan kata sandi dinamis yang dikenal dengan one-time password.

VIVAnews – Di era globaliasi saat ini, pengiriman email (electronic mail) atau surel (surat elektronik) bukan merupakan barang baru lagi, seiring dengan meledaknya penggunaan situs jejaring sosial seperti Facebook, Twitter.
Bahkan hampir semua perusahaan menggunakan layanan surel dalam meningkatkan pekerjaannya. Begitu pentingkah surat elektronik bagi sebuah perusahaan? Ketika berpikir tentang resiko yang ada membiarkan surel menjadi bagian dari sebuah perusahaan memang sungguh luar biasa, namun jika tidak mengaktifkan surel justru dinilai dapat melumpuhkan perusahaan itu sendiri.
Karena tiap perusahaan harus menyeimbangkan keamanan dan kemampuan menjalankan usaha dengan leluasa. Dibawah ini ada lima cara mudah demi keamanan surel dari virus danhacker (peretas):
Pertama, buatlah kata sandi panjang dan dinamis.
Buatlah kata sandi lebih dari 13 karakter dengan memasukan angka dan karakter khusus ke dalam kata sandi. Hal ini guna menghindari para hacker dan menyulitkannya masuk akun Anda. Atau bisa juga dengan menggunakan alat keamanan yang disebut One Time Password (OTP) Token. Karena dengan OTP yang memiliki durasi waktu validasi selama kurang dari satu menit, seorang hacker takkan mampu memecahkan kata sandi meski dengan serangan membabi-buta. Beberapa lembaga bahkan sudah menerapkan OTP online banking, E-Government, online trading, dan lain-lain. Banyak perusahaan di seluruh dunia seperti Vasco, AS, menyediakan teknologi itu. Sedangkan perusahaan di kawasan Asia yang basisnya paling dekat dengan Indonesia yang melakukan penelitian intensif, pengembangan, dan memproduksi teknologi itu adalahSecureMetric Technology Sdn. Bhd. dari Malaysia.
Kedua, aman dari penyadapan.
Dalam dunia hacker, “sniffer” adalah semacam perangkat lunak yang digunakan dapat melihat lalu lintas data dan menginterupsi pengiriman data ketika beraktifitas dalam jaringan. Bergantung kepada keamanan jaringan itu sendiri, perangkat lunak itu dapat memotong jaringan tanpa kabel dan berkabel. Cara terbaik adalah menggunakan SSL VPNdi antara pengguna dan server. SSL VPN adalah cara aman membangun kanal di Internet. Seperti contohnya salah satu produk dari AEP Networks, perusahaan Inggris dengan satu-satunya produk di dunia dengan sertifikasi FIPS Level 4, level keamanan tertinggi dan alat ini juga digunakan oleh took iTUnes milik Apple. Dengan menggabungkan SSL VPN dan OTPmaka akan menjamin keamanan surel yang lebih baik.
Ketiga, memanfaatkan Public Key Infrastructure (PKI).
Solusi keamanan pada dunia yang terhubungkan dengan network yang paling tinggi saat ini, public key infrastructure (PKI) adalah sistem pengelolaan public/privat dan sertifikat digital. Key dan sertifikat dikeluarkan oleh pihak ketiga yang dipercaya (otoritas sertifikasi, baik secara internal pada sertifikat server maupun public di dalam jaringan, seperti Verisign). Dimana pihak ketiga itu lebih umum dikenal sebagai Certificate Authority (CA). Disetiap negara yang telah mengimplementasikan PKI akan memiliki Public CA yang diakui oleh negara. Tergantung dari kebjiakan hukum setiap negara, tetapi minimal ada satu Public CA. Dan sayangnya di negara kita belum diimplementasikan. Hanya ada beberapa penyediasistem CA yang lengkap di dunia. Ada juga beberapa yang menyediakan dua versi dengan teknologi yang lebih canggih, berbayar maupun gratis. Contohnya, EJBCA adalah disediakan oleh Prime Key, sebuah perusahaan Swedia.
Keempat, mengawasi traffic dan performa.
Karena yang tak terlihat sulit dijaga, maka itu gunakan laporan untuk menandai seluruh kegiatan surel sehingga langkah cepat bisa selalu diambil. Laporan behavioral menunjukkan siapa pengirim dan penerima terbanyak serta jenis arsip atau ukuran. Jadi, anda bisa mengetahui jika ada pegawai yang melakukan kegiatan terlarang. Metode ini dapat dilakukan oleh pengelola jaringan di tiap organisasi. Bahkan, ada sistem yang sesungguhnya dikembangkan demi kepentingan pengawasan internal. Tak mudah, namun sangat efektif.
Kelima, menciptakan pembatas.
Lindungi komputer dengan antivirus dan antispam yang efektif. Firewall mesti disiapkan untuk menjaga Trojan dan memasuki sistem. Firewall ampuh menangkal phishing perangkat lunak yang melakukan aktivitas diam-diam di sistem komputer dan mencatat aktivitas untuk kemudian mengirimkan data ke seseorang atau banyak orang. Yang terburuk adalah infeksi semacam itu menjalari komputer serta jaringan. Cara paling lazim menerapkan metode ini adalah menanamkan firewall. Tingkat keamanan satu merek dan merek lain tentu saja berbeda. Namun, sebagian besar diproduksi guna menekan risiko.
Dengan lima cara mudah di atas, akun Anda akan selamat dari hacker yang aktivitasnya kini sedang meningkat di Pentagon AS, seperti dilaporkan oleh VIVAnews pada tanggal 10 Agustus 2011. Bahkan, ada peretasan yang pernah menimpa akun-akun milik TNI, dan juga dilaporkan oleh VIVAnews [Baca juga "Database Email TNI AD Dihack?"]. Pihak dari Australia bahkan telah memberitahukan dan menerbitkan beberapa informasi yang bocor dari TNI tersebut.
Serangan peretas bisa terjadi kapan pun terhadap siapa pun. Jadi, lebih baik mencegah insiden buruk yang menimpa akun anda dengan langkah mudah di atas. (WEBTORIAL)
• VIVAnews





